Integrating GitLab with Terraform and AWS Cloud
Terraform is an open-source infrastructure as code (IaC) tool created by HashiCorp. It allows users to define and provision data center infrastructure using a high-level configuration language known as HashiCorp Configuration Language (HCL), or optionally JSON. Terraform manages external resources (such as public cloud infrastructure, private cloud infrastructure, network appliances, software as a service, and more) with a ‘provider’ model. Common providers include major technology companies such as Amazon Web Services, Microsoft Azure, Google Cloud Platform, and others.

Business Use Cases for Terraform
- Multi-Cloud Deployment: Terraform supports multiple cloud providers simultaneously, allowing for complex, cross-cloud deployments. This capability helps businesses avoid vendor lock-in and optimize costs across different cloud services.
- Self-Service Infrastructure: Teams can use Terraform to spin up pre-configured, approved templates of infrastructure, enabling faster development cycles without compromising on compliance and security standards.
- Infrastructure Standardization: By codifying infrastructure, Terraform ensures that environments are reproducible and consistent. This minimizes the chances of human error during manual setups and promotes reliable, predictable deployments.
- Scalability and Automation: Terraform can handle a large number of resources across multiple providers efficiently. This scalability, combined with the ability to automate updates and maintenance tasks, supports enterprise-level operational requirements.
- Cost Management: Infrastructure as code helps in implementing policies like shutting down unused resources and scaling resources based on demand, which can significantly reduce costs.
Terraform with GitLab Integration Using AWS Cloud
Integrating Terraform with GitLab for managing AWS resources involves setting up a CI/CD pipeline that automates the deployment and management of infrastructure. Here’s how you can typically integrate these tools:
Setup Overview
- Version Control with GitLab: Store your Terraform configurations in a GitLab repository. This approach takes advantage of GitLab’s version control capabilities to track and review changes in infrastructure code.
- Automated Pipelines: Utilize GitLab CI/CD pipelines to automate the process of testing and deploying the Terraform configurations. Pipelines can be configured to trigger on commits, merging requests, or manual requests.
- AWS Integration: Configure Terraform to manage AWS resources by using the AWS provider. The AWS credentials and access controls should be securely managed, often using environment variables or encrypted secrets in GitLab.
Typical Pipeline Steps
- Initiate: Initialize Terraform configurations in the pipeline. This step sets up Terraform to manage the specified resources.
- Plan: Execute
terraform planto preview changes without applying them. This helps in reviewing potential impacts before changes go live. - Apply: Run
terraform applyto apply the planned changes to your AWS environment. This step can be set to manual to require approval, ensuring changes are reviewed.
Security and Compliance
- Audit Trails: All changes are recorded in Git and GitLab, providing a comprehensive audit trail of who made changes and when.
- Policy as Code: Integrate policy-as-code tools like Terraform Sentinel to enforce organizational policies automatically during the Terraform plan and apply stages.
- Secure Secrets Management: Use GitLab’s secure variables or integrate with AWS Secrets Manager to manage sensitive data like AWS access keys.
For Integration of GitLab with Terraform as Infrastructure as code as step by step guide
Integrating Terraform with GitLab for managing AWS Cloud resources involves setting up a CI/CD pipeline. This pipeline automates the process of testing, planning, and applying Terraform configurations to AWS. Here’s a step-by-step guide to achieve this integration:
Step 1: Setup Your GitLab and AWS Accounts
- GitLab Account: Ensure you have access to a GitLab account. If not, sign up at GitLab’s website.
- AWS Account: Make sure you have an AWS account. Configure your AWS credentials securely. Typically, for automation, you will use an IAM user with appropriate permissions.
Step 2: Create a GitLab Repository
- Create a New Repository: On your GitLab dashboard, create a new project to store your Terraform configurations.
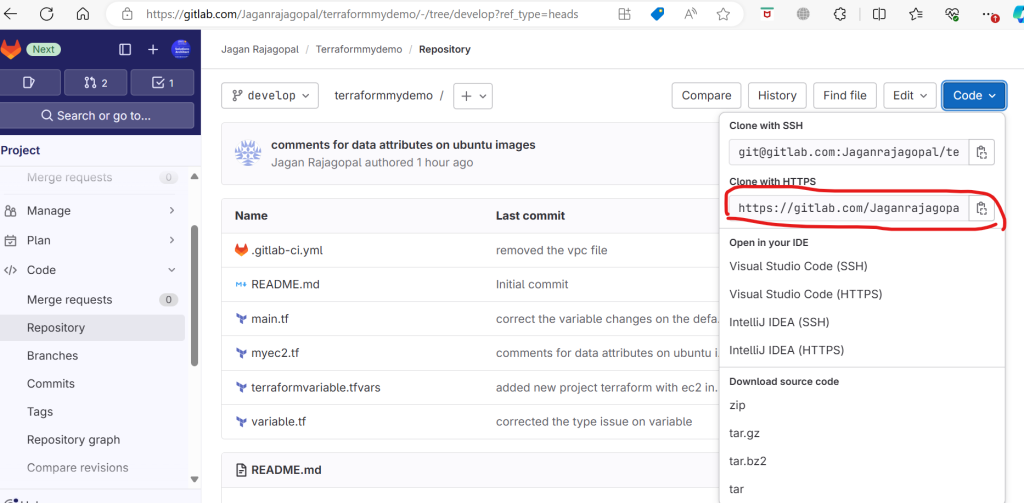
- Clone the Repository: Clone the repository to your local machine using Git.
Step 3: Write Terraform Configurations
- Terraform Files: In your local repository, create Terraform configuration files (
.tf) to define the required AWS resources.main.tf: Define provider and resources.variables.tf: Define variables used in configurations.outputs.tf: Specify output parameters.
Example main.tf:
Clone the project into download local file :
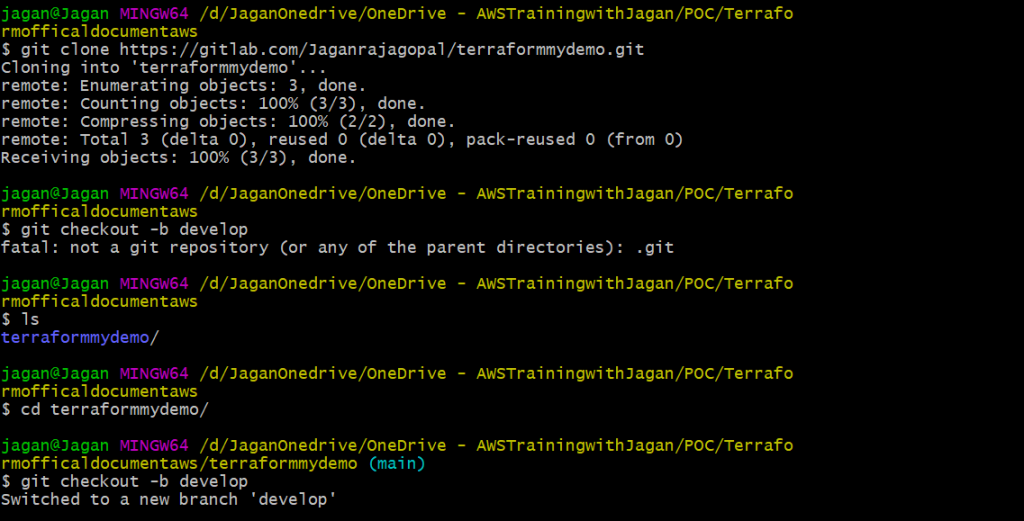
Step 4: Configure GitLab CI/CD Pipeline
- Create
.gitlab-ci.ymlFile: In the root of your repository, create a.gitlab-ci.ymlfile to define the pipeline stages and jobs. - Define Stages: Typical stages include
init,validate,plan, andapply.
Example .gitlab-ci.yml:
image: registry.gitlab.com/gitlab-org/terraform-images/stable:latest
variables:
TF_ROOT: ${CI_PROJECT_DIR}
TF_ADDRESS: ${CI_API_V4_URL}/projects/${CI_PROJECT_ID}/terraform/state/${CI_PROJECT_NAME}
AWS_ACCESS_KEY_ID: ${AWS_ACCESS_KEY_ID}
AWS_SECRET_ACCESS_KEY: ${AWS_SECRET_ACCESS_KEY}
AWS_DEFAULT_REGION: ${AWS_DEFAULT_REGION}
cache:
key: example-production
paths:
- ${TF_ROOT}/.terraform
before_script:
- cd ${TF_ROOT}
stages:
- prepare
- validate
- build
- deploy
init:
stage: prepare
script:
- gitlab-terraform init
validate:
stage: validate
script:
- gitlab-terraform init
- gitlab-terraform validate
plan:
stage: build
script:
- gitlab-terraform plan
- gitlab-terraform plan-json
artifacts:
name: plan
paths:
- ${TF_ROOT}/plan.cache
reports:
terraform: ${TF_ROOT}/plan.json
# Separate apply job for manual launching Terraform as it can be destructive
# action.
apply:
stage: deploy
environment:
name: production
script:
- gitlab-terraform apply
dependencies:
- plan
when: manual
only:
- main
Please find the complete the GitLab source code:Files · develop · Jagan Rajagopal / terraformawsv2 · GitLab
Step 5: Secure Your AWS Credentials
- Environment Variables: Store your AWS credentials (
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY) as protected environment variables in GitLab.- Go to your GitLab project > Settings > CI/CD > Variables.
- Add your AWS credentials here.
Step 6: Test and Deploy
- Push Changes: Commit your Terraform files and the
.gitlab-ci.ymlto your GitLab repository. - Monitor Pipeline: Go to CI/CD > Pipelines in your GitLab project to monitor the execution of your pipeline.
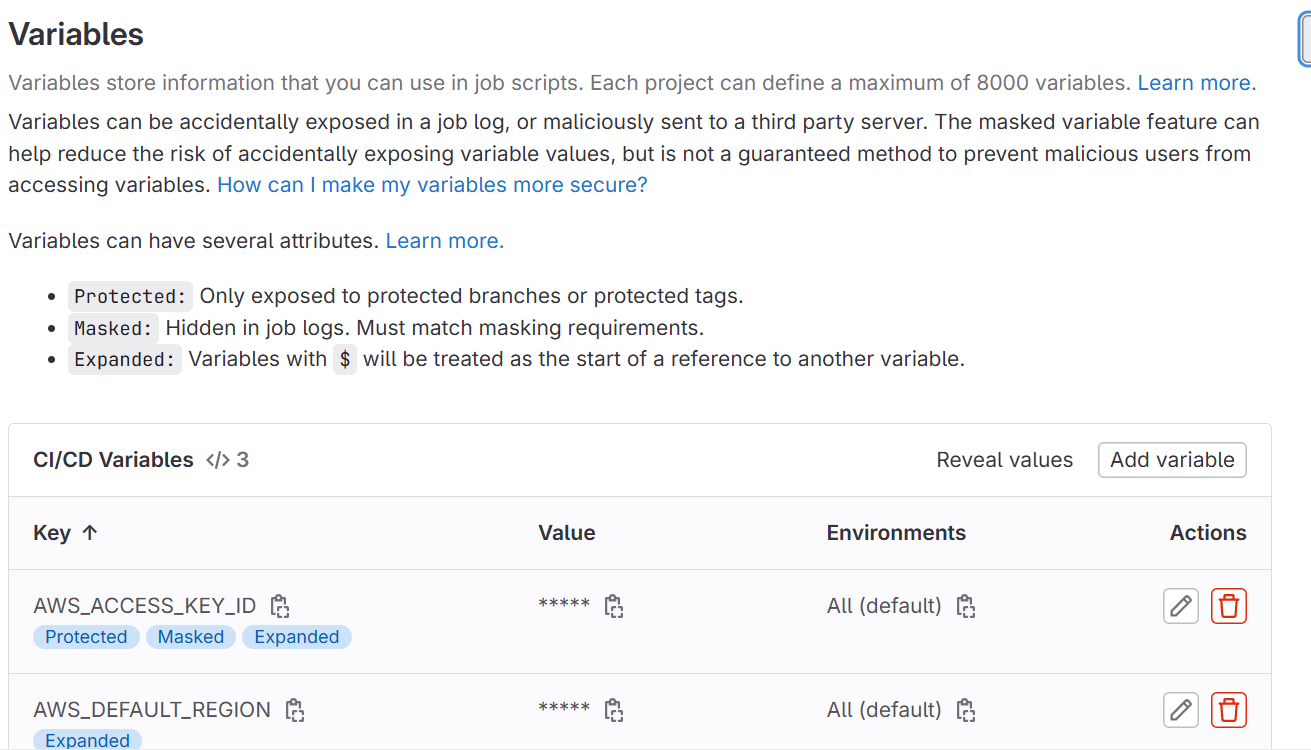
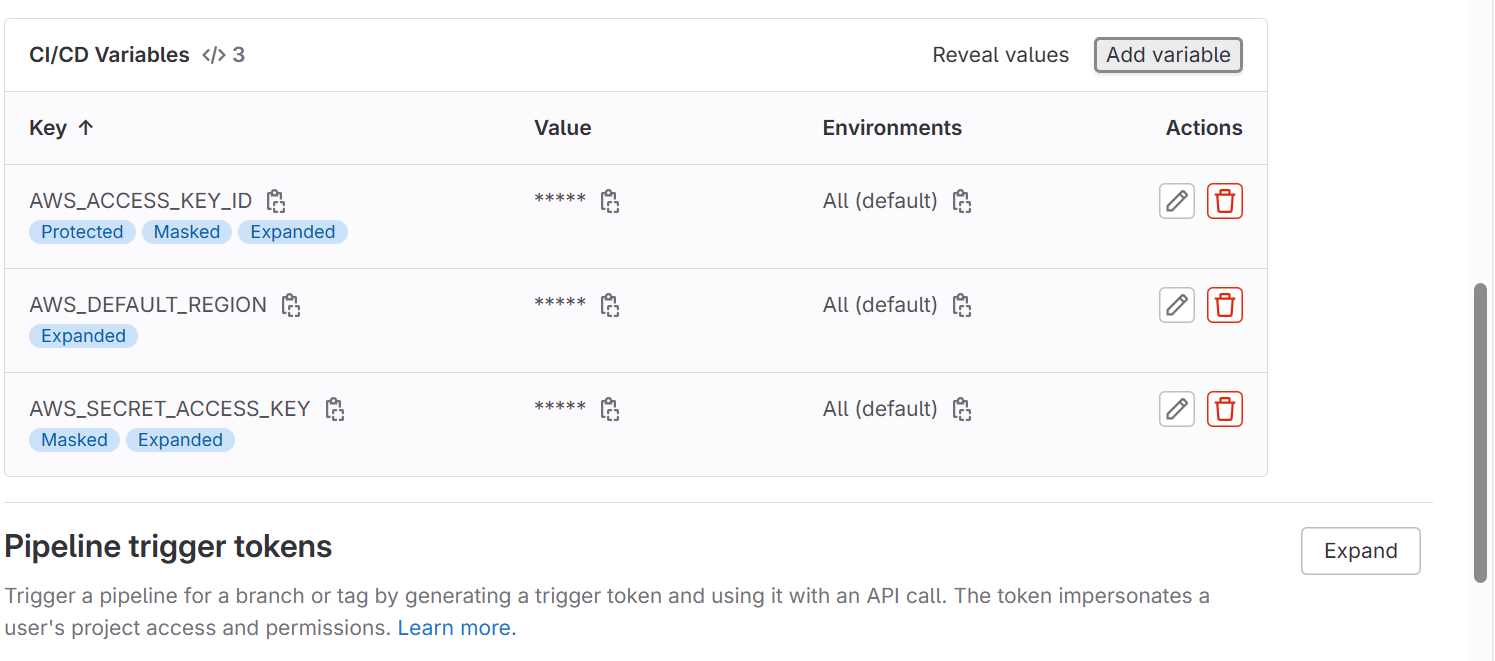
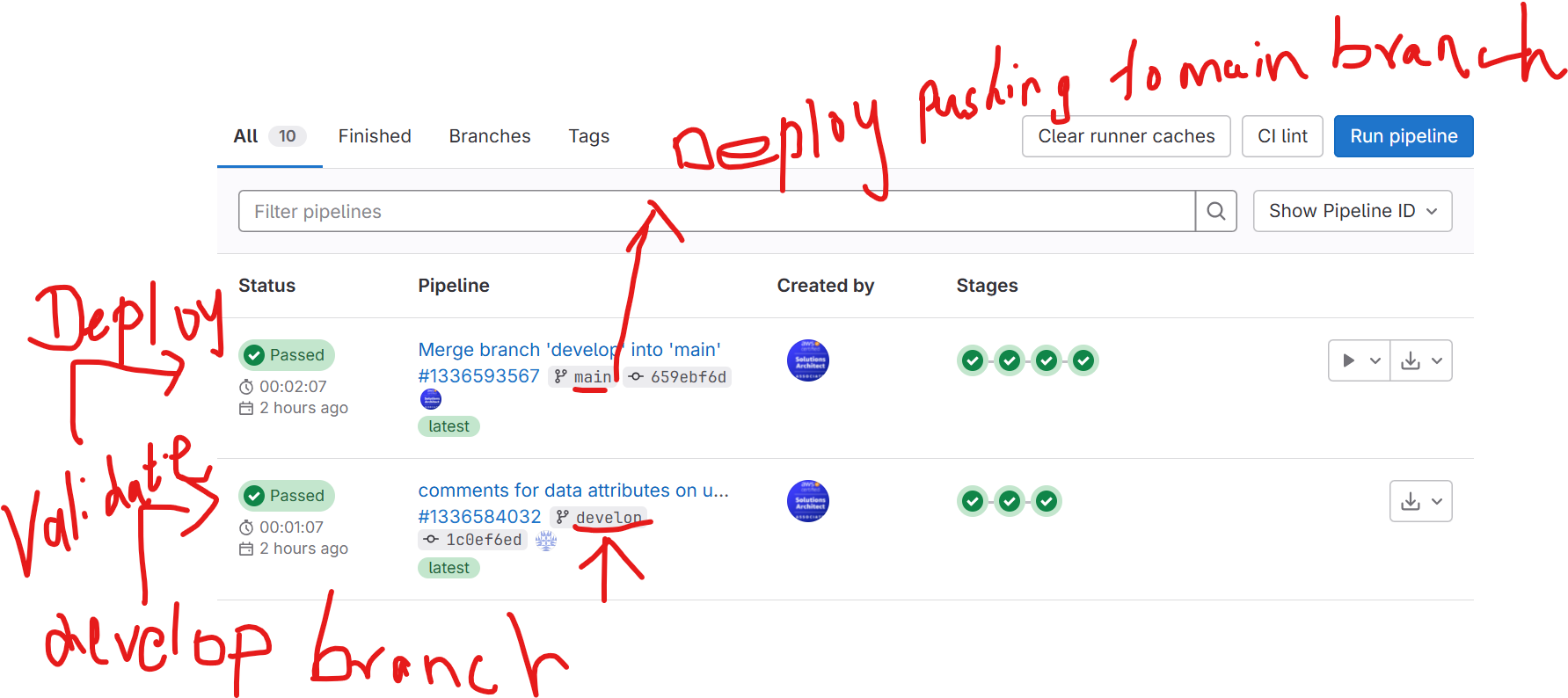
- You have to check into develop branch , it will validate and build
Please find the My pipeline reference:Pipelines · Jagan Rajagopal / Terraformmydemo · GitLab
2. Manual Trigger: When you merge the branch on the main branch by using MR request , it will automatically trigger into Main branch
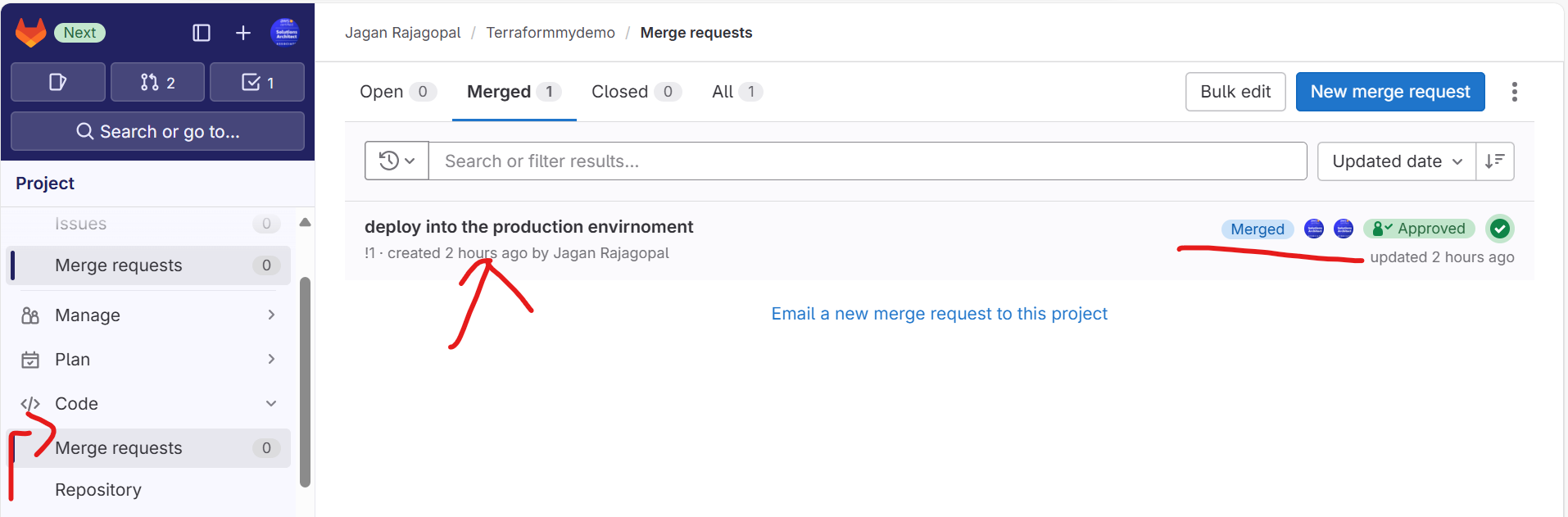
Step 7: Review and Iterate
- Review Outputs: Check the outputs and logs from the pipeline to ensure your infrastructure is deployed as expected.
- Iterate: Update your Terraform configurations as required and push changes to repeat the process.
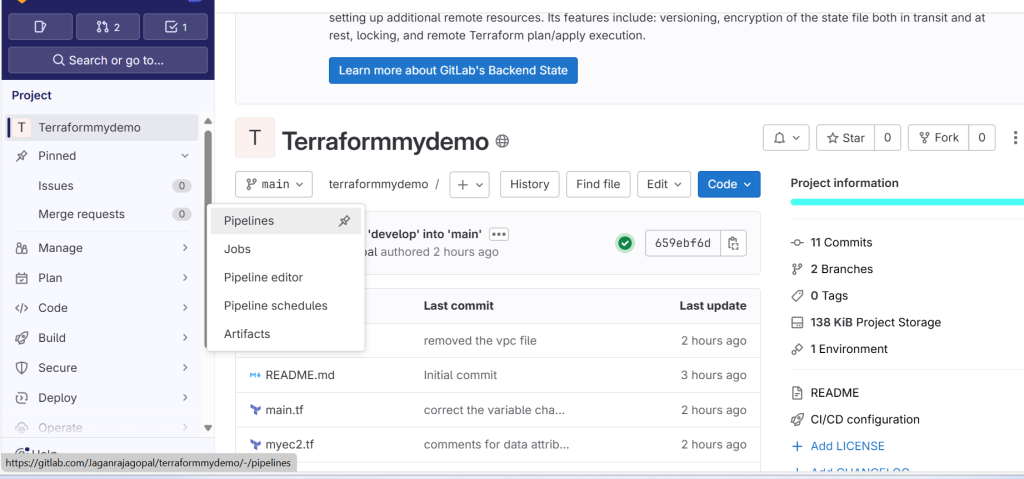
This setup provides a robust method for managing AWS resources through Terraform, leveraging GitLab’s CI/CD capabilities to automate and streamline the process. It ensures that changes are reviewed and applied in a controlled and predictable manner.