DevOps Architecture for Scalable Containerized Deployments with Amazon EKS, GitLab, and Terraform
This architecture represents a DevOps pipeline for deploying, managing, and monitoring containerized applications using Amazon EKS, Helm, GitLab CI/CD, and Prometheus for monitoring. It leverages Terraform for Infrastructure as Code (IaC) and integrates with several AWS services like Amazon ECR, Amazon RDS, Amazon ElastiCache, and Amazon CloudWatch. The goal is to automate the deployment process, monitor the application’s performance, and ensure the infrastructure is secure and scalable. The architecture also incorporates AWS Key Management Service (KMS) for security and Amazon S3 for backups.
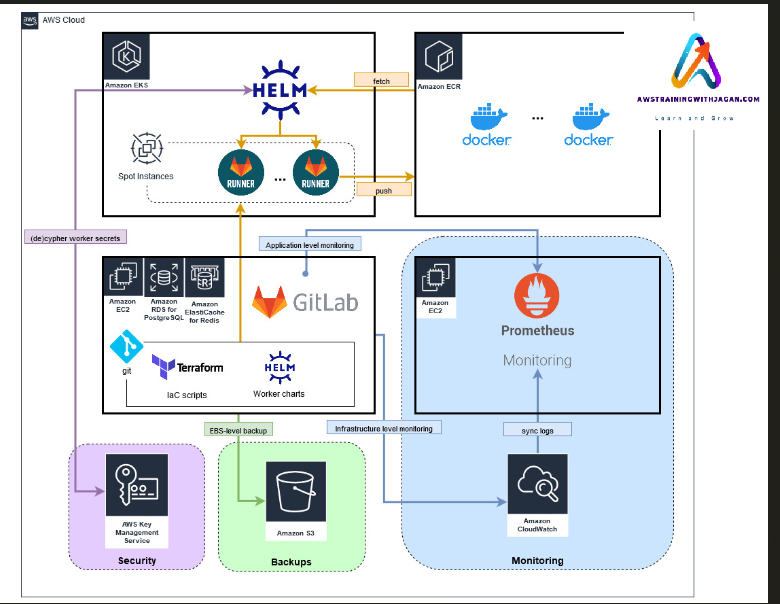
Kubernetes for container orchestration, monitoring tools, and GitLab CI/CD for automation. Let me break it down by its key components:
1. Amazon EKS (Elastic Kubernetes Service):
- Role: EKS is the managed Kubernetes service on AWS used here for orchestrating Docker containers.
- Helm: Helm is used to manage Kubernetes applications with Helm charts, which are YAML files that define the application infrastructure.
- Spot Instances: Spot instances (economical EC2 instances) are used as worker nodes for running containers on the EKS cluster, optimizing costs.
2. GitLab CI/CD and Runner:
- GitLab: This GitLab instance is the central component for managing version control, CI/CD pipelines, and deployments.
- GitLab Runners: These runners execute the CI/CD jobs (build, test, deploy) for applications.
- Push to Amazon ECR: The runners fetch Docker images from Helm charts and push these images to Amazon ECR (Elastic Container Registry). ECR is AWS’s Docker image repository.
- Deploy to EKS: After the images are stored in ECR, they are pulled and deployed on the EKS cluster.
3. Infrastructure Management (Terraform):
- Terraform: Infrastructure-as-Code (IaC) tool is used to provision the necessary AWS infrastructure (EC2, RDS, EKS, etc.) using predefined scripts.
- IaC and Helm Worker Charts: The architecture uses a combination of IaC scripts for provisioning infrastructure and Helm charts for deploying applications on EKS.
4. Application and Infrastructure Monitoring:
- Application Monitoring (Prometheus): Application-level monitoring is handled by Prometheus, which pulls metrics from various sources, including the Kubernetes pods running on EKS. It provides deep insights into the health and performance of the applications.
- Amazon CloudWatch: This service is integrated for infrastructure-level monitoring to keep track of logs, metrics, and alerts for AWS resources like EC2 and EBS (Elastic Block Store).
5. Secrets Management:
- AWS KMS (Key Management Service): KMS is used for encrypting and decrypting worker secrets such as environment variables, API keys, and database credentials, ensuring that sensitive information remains secure.
6. Databases:
- Amazon RDS for PostgreSQL and Amazon Elasticache for Redis: These managed database services are used for relational (PostgreSQL) and caching (Redis) needs, respectively.
7. Backup and Recovery:
- Amazon S3 for EBS-Level Backups: The architecture ensures that EBS (Elastic Block Store) volumes attached to EC2 instances are backed up to Amazon S3, enabling reliable data recovery and long-term storage.
8. Security:
- AWS Key Management Service (KMS): In addition to managing secrets, KMS also provides encryption at rest for data stored in S3, EBS, and other services, ensuring that backups and application data are secure.
9. Worker Node Monitoring:
- Amazon EC2 with Prometheus: EC2 instances used in this architecture are monitored by Prometheus, which collects and syncs logs to maintain an overview of worker node health and performance.
Summary of Workflow:
- Developers push their code to GitLab.
- GitLab CI/CD triggers runners to build the Docker image, using Helm charts to fetch the application configuration and deploy it to the EKS cluster.
- The built image is stored in Amazon ECR and pulled by the EKS cluster for deployment.
- Application and infrastructure metrics are monitored using Prometheus and Amazon CloudWatch, while logs are synced and monitored.
- Backup operations are handled through Amazon S3 for EBS-level backups.
- The architecture integrates AWS KMS to manage secrets securely and ensure data encryption.
This setup highlights a robust and scalable solution for deploying containerized applications on AWS using Kubernetes (EKS) and CI/CD best practices with GitLab, Terraform, and Helm.
Business Use Cases:
This architecture is ideal for businesses aiming to:
- Automate CI/CD Pipelines: It enables seamless continuous integration and continuous delivery (CI/CD) using GitLab and GitLab Runners, allowing teams to automate building, testing, and deploying applications.
- Containerized Application Deployment: Using Amazon EKS and Helm, businesses can deploy and scale containerized applications efficiently. Helm simplifies Kubernetes management by providing reusable templates for application configuration.
- Scalable Infrastructure Management: Terraform provides IaC, making it easy to manage and scale the infrastructure, including databases, storage, and compute instances, by using simple scripts.
- Application and Infrastructure Monitoring: With Prometheus and Amazon CloudWatch, businesses can monitor both their applications and infrastructure in real-time. This ensures the reliability of applications through proactive monitoring and logging.
- Database and Caching Solutions: The use of Amazon RDS for PostgreSQL and Amazon ElastiCache for Redis ensures the architecture supports reliable relational databases and caching for faster application performance.
- Secure Secrets Management: AWS KMS ensures that sensitive information (like API keys and credentials) is securely managed and encrypted, a critical feature for industries handling sensitive data such as finance, healthcare, or e-commerce.
- Backup and Disaster Recovery: Amazon S3 is used for EBS backups, ensuring that business-critical data is protected and can be restored in case of failures.
When to Use This Architecture:
- High Scalability Needs: If your business requires the ability to scale applications quickly (up or down), especially for high-traffic or dynamic workloads, this architecture is ideal because it uses Amazon EKS with Spot Instances and Kubernetes’ inherent scaling capabilities.
- Continuous Deployment & Development: Businesses following agile practices with frequent code deployments will benefit from the automated CI/CD pipeline, allowing developers to push new features rapidly and reliably.
- Microservices Architecture: If your application architecture is based on microservices where different services need to be deployed independently, Kubernetes combined with Helm and GitLab provides a flexible and efficient solution.
- Cloud-Native Applications: This architecture is suitable for businesses that are already cloud-native or planning to migrate to the cloud and require a cloud-first approach using AWS’s managed services for containers, databases, and monitoring.
- Infrastructure as Code (IaC) Adoption: If you want to manage infrastructure using IaC for automation, version control, and repeatability, Terraform is a powerful tool integrated into this pipeline.
- Security and Compliance: For businesses that need to meet strict security or compliance standards, using AWS KMS for encryption and secure secrets management adds an extra layer of protection for sensitive data and workloads.
- Backup and Disaster Recovery: Companies that require regular backups for disaster recovery purposes will benefit from the Amazon S3 integration for storing and managing backups securely.

